NextGig Systems, Inc. - Network Connectivity & Test Solutions

Gigamon - Tap Aggregation, Regeneration and Filtering to enable Deep Packet Inspection (DPI) in Carrier IP Networks
Silicon Valley, CA - March 09, 2007 – The weapon of choice for service-oriented network monitoring is Deep Packet Inspection (DPI). Typically, DPI is performed by high-performance software solutions that run on standard server hardware platforms, enabling providers to identify, classify or even selectively block IP traffic. DPI is used to detect and protect against security threats and network anomalies, and facilitate wiretapping and reconstruction of relevant digital transactions.
For the technology to work, DPI must be able to unobtrusively acquire a high-fidelity replica of production traffic from multiple sources across a triple redundant network. Recently, instead of using conventional network taps, the Data Access Network (DAN) has emerged as the “Best Practice” data access and network monitoring architecture for cost-effective DPI monitoring. The DAN architecture is currently being deployed by several major carriers in nationwide rollouts. DAN has proven to save tens of millions of dollars for these telecom customers by passively tapping and aggregating tapped traffic from multiple network links, separating Service-over-IP (SoIP) from non-SoIP data using hardware based packet filters, and regenerating and logically mapping the aggregated SoIP traffic to multiple DPI analyzers in order to optimize traffic load.
Technical Challenges
The technical challenge for DPI monitoring is akin to that of searching for pins in a haystack; more precisely, searching for fragments of pins from multiple gigantic haystacks.
Recall that Ethernet was designed for data. It was meant for asynchronized transmission of data broken up into fragments (i.e., packets), where the timing and the temporal order between fragments are not important. So when someone surfs the web making random requests for packets from all over the world, packets will arrive in different order and at different time slots. Some of them don't even arrive at all. The protocol embedded in Ethernet makes allowance for such chaos and diligently reassembles the fragments in proper order and make repeated requests if they are lost. This works for data and surprisingly works for voice and video as well, in spite of the fact that digital voice and digital video are synchronized traffic. Since in this case, the order and the timing between the fragments are indeed important.
One reason why Ethernet works even for SoIP is because the pipes that make up the carrier networks are relatively large and under-utilized; therefore SoIP packets typically travel unhindered. Moreover, customer’s state-of-the-art fully meshed networks are redundant and parallelized such that there are multiple paths for the packets to travel. On the other hand, when a network engineer has to make an independent measurement of the network’s performance as it is utilized for SoIP transmission (in order to ensure SLA, e.g.), or when a law enforcement officer is given the mandate to track potentially illicit discourse, the fact that SoIP packets are never retransmitted (such that every single packet must be collected) and that there are unlimited paths for them to travel have imposed a huge problem. In other words, how does one comb through multiple haystacks in order to find all of the random fragments (packets) of a pin?
DAN to enable Tap Aggregation and Regeneration for DPI
DAN is often described as the distributed "Data Socket" for out-of-band network monitoring. The Data Access Switch, which is the building block of the DAN, is like a vacuum cleaner that sucks up the hay wherever they might exist, filters out metal fragments that possess characteristics which would materialize into a pin, and presents these relevant pieces to the DPI analyzer in order to recreate the original puzzle.
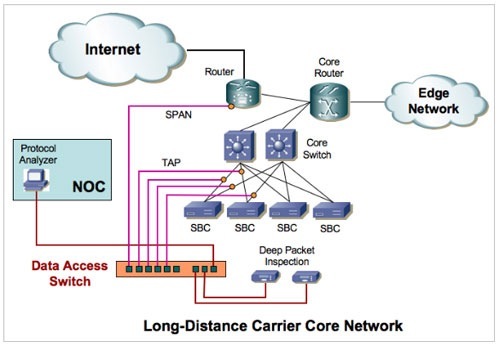
The diagram above shows a commercial SoIP network. This is the core network typical of a long distance carrier which has a number of redundant core switches that manage traffic in and out of the SBC (Session Border Controller) and core routers that manage signaling and SoIP traffic that goes out to other switch centers (edge networks) or to the Internet. If one were to attach a DPI analyzer directly to the network, the amount of traffic would be so overwhelming that it will easily oversubscribe the tool. Moreover, so many individual tools would have to be deployed in order to fully capture all of the relevant packets from disparate critical locations across the network that no customer can ever cost-justify such a deployment.
Instead, telecom customers use a number of passive network taps to tap all of the redundant optical Gigabit links connecting the SBC to the switch, copy and filter the traffic using the Data Access Switch either to extract RTP (voice) or RTCP (signaling) packets, regenerate and map (i.e., load-share) the aggregate to multiple DPI analyzers. In addition, the Data Access Switch can accept SPAN port data from the router to monitor outgoing traffic. Finally, for troubleshooting purpose, a protocol analyzer remotely located at the central NOC can be connected to the data access switch, which would be shared among the switching centers (and houses the highly skilled network engineers).
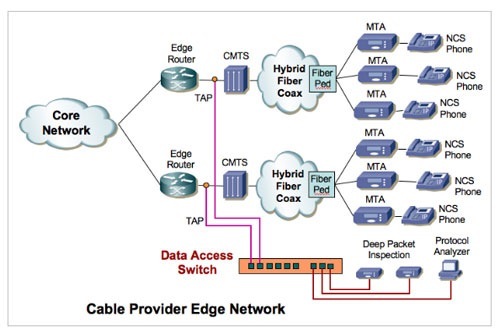
Besides the core, telecom carriers are also deploying Data Access Networks at the edge (see above), where basically the same connectivity functions are performed at the neighborhood hubs, passively tapping all of the Gigabit copper links that connect the CMTS (Cable Modem Termination Systems) to the edge routers, and aggregating, regenerating and filtering SoIP traffic for DPI monitoring.
In summary, network monitoring using DPI analyzers is a mission critical application that is tailor-made for the Data Access Network (DAN) architecture, which aggregates traffic from multiple taps, regenerates and filters aggregate traffic both at the core and the edge, and saves substantial amounts of money for the telecom carrier.
About Gigamon
Gigamon is the inventor and leading provider of Data-Access Switches. Its flagship product, GigaVUE®, can multicast packets from one span or tap to many tools to solve the span port sharing problem. It also can aggregate and intelligently filter packets from many spans or taps to one or multiple tools to solve the problem of monitoring flows across complex mesh topologies and virtual networks. GigaVUE® facilitates unobtrusive parallel tool deployment with network-wide coverage, significantly reducing customers’ capital budgets and yielding immediate ROI benefits.
For more information about Gigamon Data Access Switches please contact us here.



Questions? Call 1-805-277-2400
Web Demo
Related Products
All Network Taps
Network Monitoring
Network Recording
Ethernet Testing
Network Emulation
Storage Emulation

All registered and unregistered trademarks are the sole property of their respective owners.
Products | Solutions | Store | Support | News | About Us | Why NextGig? | Employment | Privacy | Sitemap | Contact Us
Copyright © NextGig Systems, Inc. All Rights Reserved.